Impact Awareness – bounty submission
Summary
Given the fact that your bounty report might change your finding from being “accepted” and even your reward over a particular program, it’s essential to provide enough information such as the impact and what/how it can be accomplished (including combinations with different attacking vectors) with examples/pocs. If possible, providing solutions to mitigate the problem can also be helpful as the person who’s reading your report might not have an advanced knowledge across the area you’re exploring.
As an example, I’ll share one of my findings here that I was expecting a small bounty (e.g., USD ~100,00) for disclosing information due to a misconfiguration within the application I was assessing and it turned out that my focus on the report totally made the difference as it was even rewarded with an additional of $130 bonus (besides $477.20). Kindly refer to the following where I’m just obfuscating a few details due to a Synack’s private program:
Description

Impact

PoC

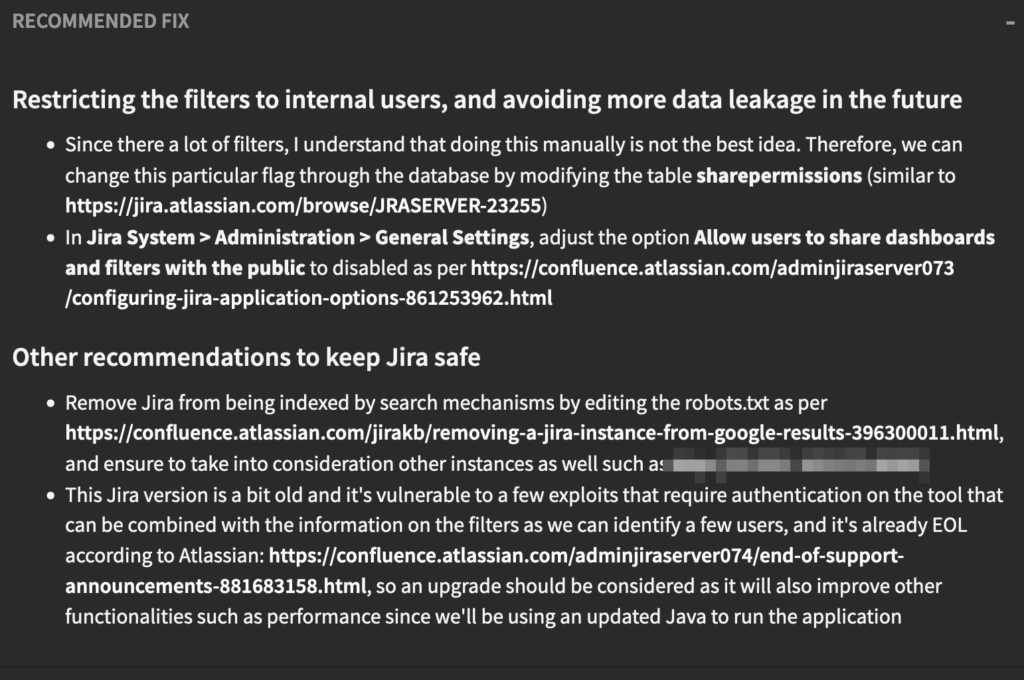
Recommended Fix
References
- Writing bug bounty reports:
- https://blog.yeswehack.com/yeswerhackers/tips-write-report-bug-bounty/
- https://dewcode.medium.com/how-to-write-a-good-bug-bounty-report-in-just-10-minutes-980a0a1b1b18
- More about the finding above:
- https://medium.com/@logicbomb_1/bugbounty-nasa-internal-user-and-project-details-are-out-2f2e3580421b
